Enhanced IT Protection
We provide advanced cybersecurity products and services to protect your organization from threats while meeting Compliance requirements.
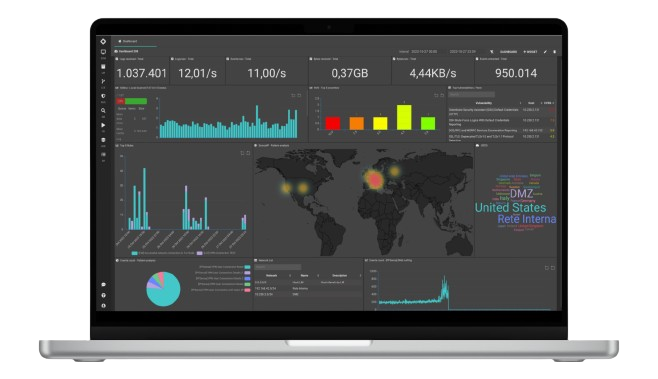
IT Vendor at your side in daily security challenges
SecureGate operates in the IT Security sector with the goal of enhancing corporate security posture through a comprehensive and customizable offering, consisting of IT products and managed cybersecurity services.
Through a “Security by design” approach, SecureGate strengthens the cybersecurity of organizations by automating sensitive data controls and developing a robust IT infrastructure protection strategy.
Years of experience and a high level of technical expertise enable SecureGate to anticipate industry trends and stay up to date with the evolution of cyberattacks.
We aim to support companies in their digital transformation process by developing a strong and ongoing IT security strategy.
We strongly believe that cybersecurity is one of the key assets upon which to build corporate development strategies.
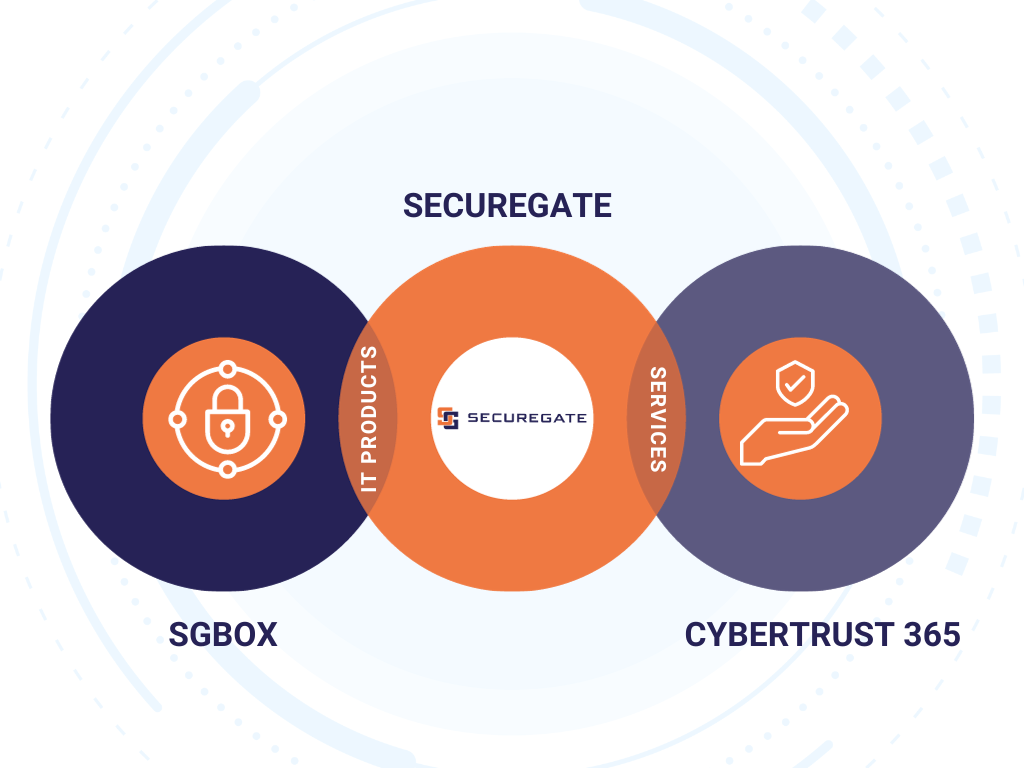
SecureGate offer is developed through two Business Unit: SGBox and CyberTrust 365
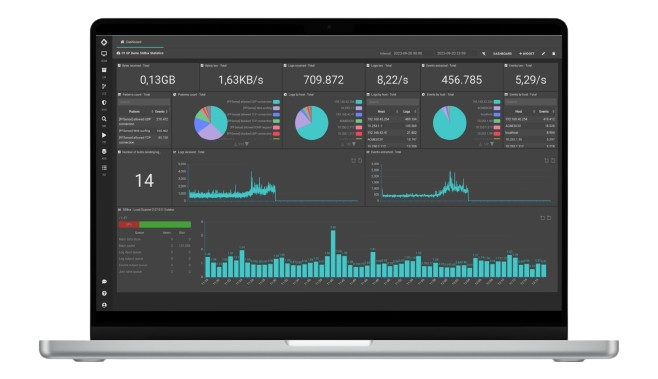
SGBox - SIEM & SOAR Platform

SGBox is a Next Generation SIEM & SOAR Platform offering different solutions for controlling and managing ICT Security.
Its modular and distributed architecture means it can adapt to the various company needs
CyberTrust 365 - Managed Security Service Provider

CyberTrust 365 is the Business Unit dedicated to Managed Cybersecurity Services.
24/7 monitoring, proactive defense and in-depth threat analysis: we manage all of your cybersecurity activities for you to focus on your core business.
Why rely on SecureGate
Specific Expertise
Our team of IT developers and engineers have specific and up-to-date technical skills to develop solutions that keep pace with the evolution of attacks and proactively intervene.
Integrated Management of Cybersecurity
We take care of every aspect of cybersecurity, starting from the real needs of protecting sensitive data.
Strategy Design and Development
We define the best strategy to develop for your organization, starting from a first phase of support to the actual implementation.
Compliance with Regulations
The collection of information from security events is carried out in compliance with the privacy regulations of different countries.





